When you hear “access control”, the first words that come in your mind will probably be “safety”, “security”, “badge” or even “doors”. The reality however is far more complex than that: allow us to explain why !
You might be an access control engineer specialist or simply a curious amateur passionate by technologies and mechanics driven by learning new things, well you are at the right place ! For clarity reasons, we will explain how it works by taking our own access control solution as an example.
Which equipment is necessary to have a complete access control solution ?
Starting from the beginning, which means defining what an access control solution truly is. This solution is used in order to control the entrance and exits of a structure (it can be a company’s building, banks, shops etc…) or for private spaces such as parking lot or a private residence. It is composed of several technical elements which, put together, form an access control system.
Our solution, for instance, is composed by a badge reader, a pilot and power supply card, both designed with an Ethernet POE interface which enables the wiring and the management, and last but not least an USB reader.
How does it genuinely work ?
Our badge reader allows to collect the information which comes from the contactless cards, and/or phones equipped with the NFC technology, to send them to a server. This latter will control the pilot card. Moreover, you can have the control by the distance of the authorizations and the access control modifications thanks to the connexion between the badge readers and your ethernet network.
Quick reminder: our readers have the ability to read not only the majority of contactless card with 13.56MHz existing on the market, but also the phones equipped with the NFC technology.
The pilot card has 3 relays and 3 entrances in order to connect doors strikers, opening buttons and so on and so forth.
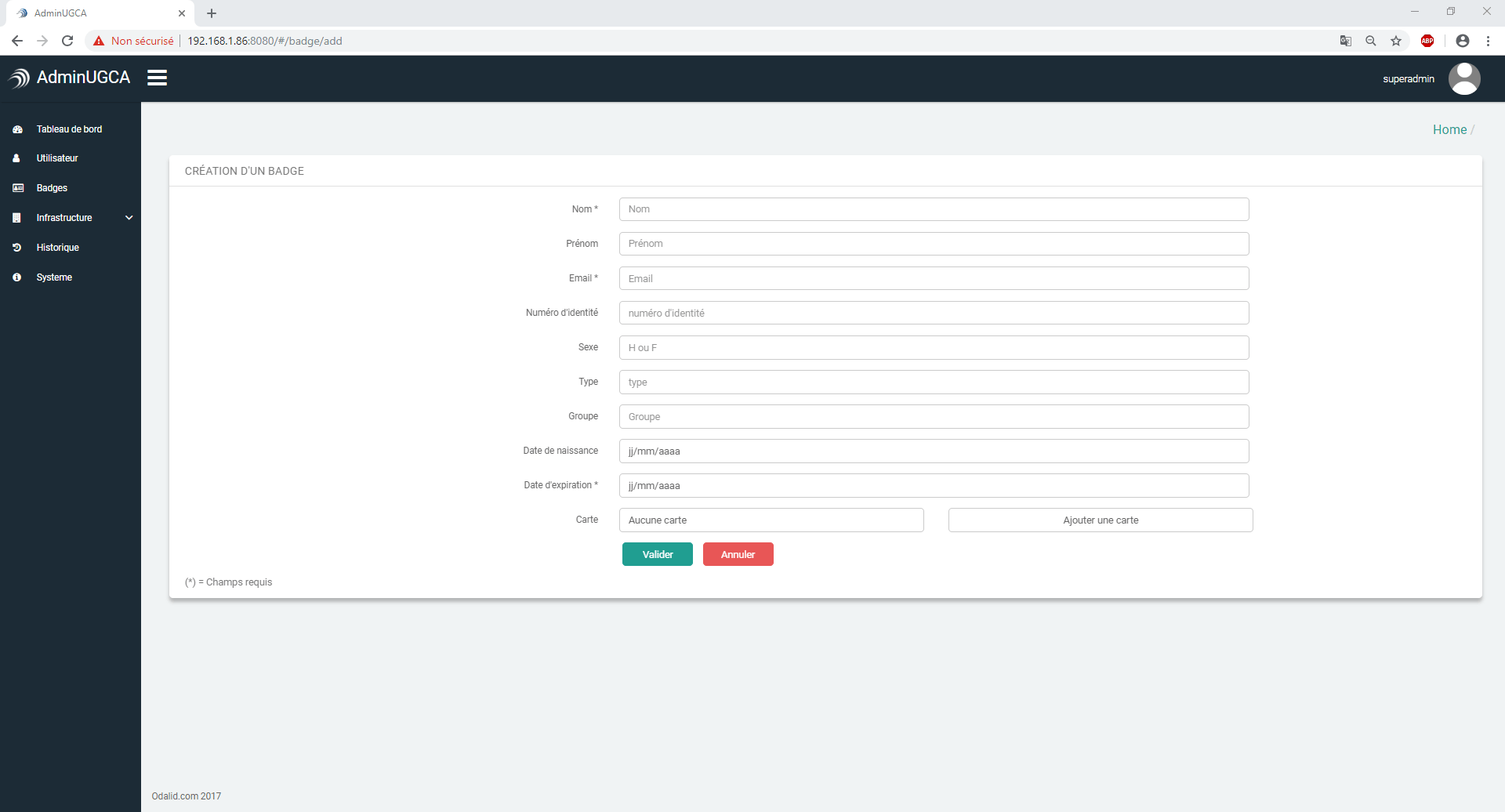
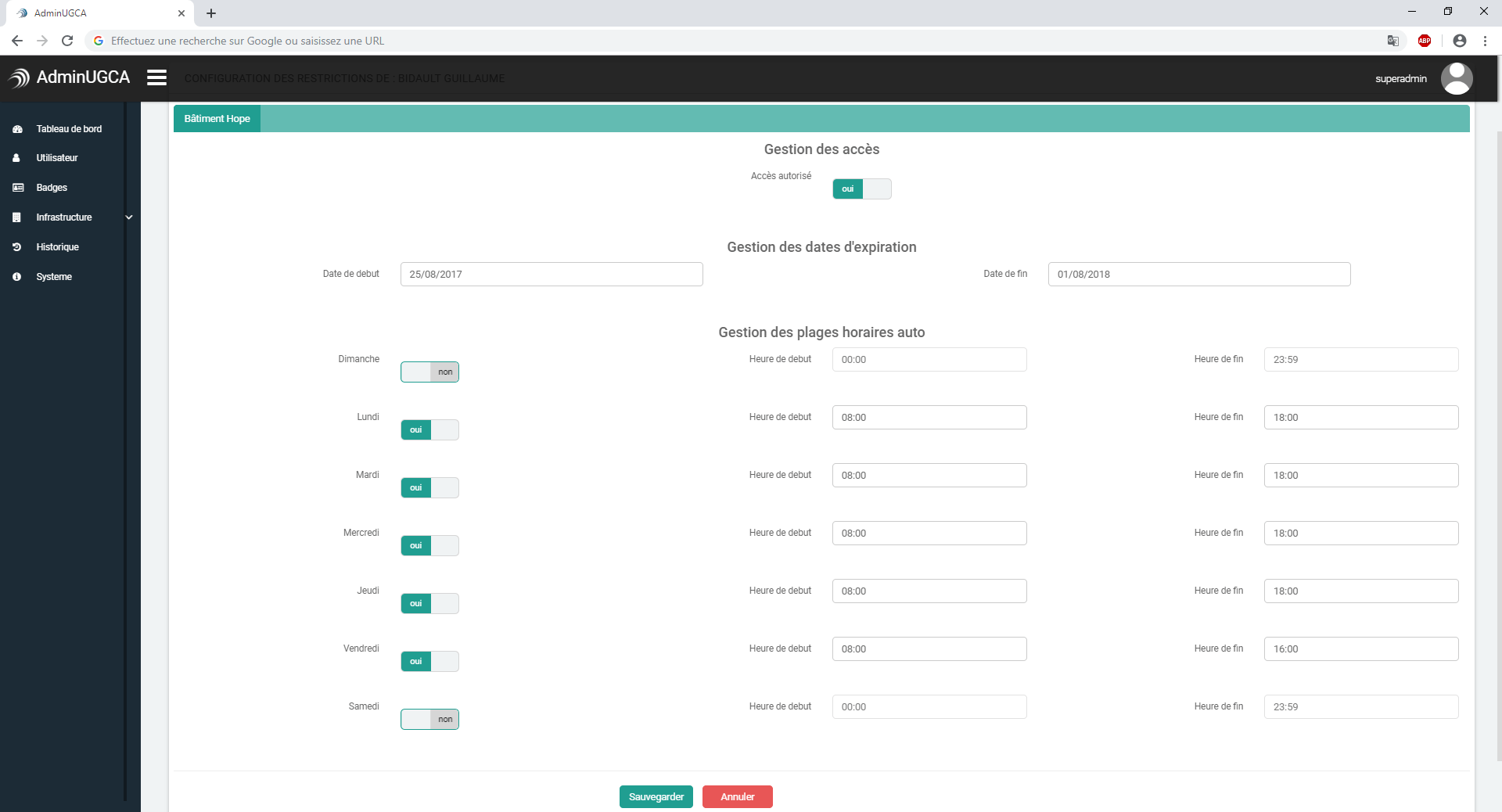
Thanks to its web interface, the management software allows to manage the time slots, access zones, see the flows historic on any platform which has a connexion with the server. The connexion with this software is done safely via a login password.
In brief, behind the term ‘’access control’’ several technical elements are hidden, which once put together give us a whole access management solution.
Software interface (API) :
Click here to find out more about our products and solutions !